Research
My research focus is on Security of Networked Systems with a special focus on virtualized networking resources and platforms including Software Defined Networking and Virtual Machines. I also have experience in the area of Sensor Networks/Internet of Things, Network Coding, Embedded Systems and Machine Learning. Here is an overview of my past and current research projects:
IEEE TNSM 2020 - MLSNet: A Policy Complying Multilevel Security Framework for Software Defined Networking
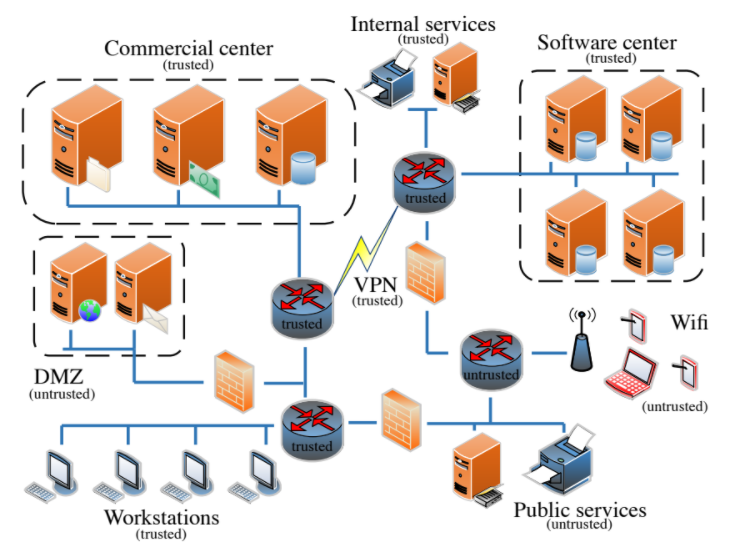
Abstract - Ensuring that information flowing through a network is secure from manipulation and eavesdropping by unauthorized parties is an important task for network administrators.
Many cyber attacks rely on a lack of network-level information
flow controls to successfully compromise a victim network. Once
an adversary exploits an initial entry point, they can eavesdrop
and move laterally within the network (e.g., scan and penetrate
internal nodes) to further their malicious goals. In this paper, we
propose a novel multilevel security (MLS) framework to enforce a
secure inter-node information flow policy within the network and
therein vastly reduce the attack surface available to an adversary
who has penetrated it. In contrast to prior work on multilevel
security in computer networks which relied on enforcing the
policy at network endpoints, we leverage the centralization of
software-defined networks (SDNs) by moving the task to the
controller and providing this service transparently to all network
nodes. Our framework, MLSNet, formalizes the generation of a
policy compliant network configuration (i.e., set of flow rules
on the SDN switches) as network optimization problems, with
the objectives of (1) maximizing the number of flows satisfying
all security constraints and (2) minimizing the security cost
of routing any remaining flows to guarantee availability. We
demonstrate that MLSNet can securely and efficiently route flows
that satisfy the security constraints and route the remaining flows
with a minimal security cost (e.g., route > 85% of flows, where
the heuristic achieves 89% and 87% of the optimal solutions for
the optimization problems).
IEEE TNSM 2018 - Fast Network Configuration in Software Defined Networking
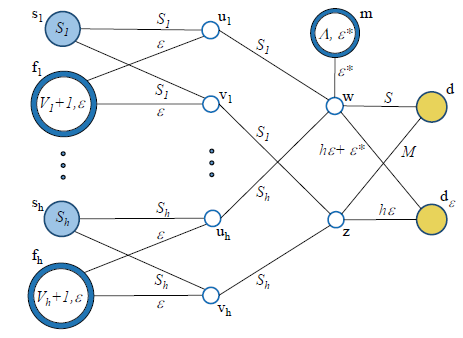
Abstract - Software Defined Networking (SDN) provides a
framework to dynamically adjust and re-program the data plane
with the use of flow rules. The realization of highly adaptive SDNs
with the ability to respond to changing demands or recover after
a network failure in a short period of time, hinges on efficient
updates of flow rules. We model the time to deploy a set of flow
rules by the update time at the bottleneck switch, and formulate
the problem of selecting paths to minimize the deployment time
under feasibility constraints as a mixed integer linear program
(MILP). To reduce the computation time of determining flow
rules, we propose efficient heuristics designed to approximate
the minimum-deployment-time solution by relaxing the MILP or
selecting the paths sequentially. Through extensive simulations
we show that our algorithms outperform current, shortest path
based solutions by reducing the total network configuration time
up to 55% while having similar packet loss, in the considered
scenarios. We also demonstrate that in a networked environment
with a certain fraction of failed links, our algorithms are able to
reduce the average time to reestablish disrupted flows by 40%.
IEEE TNSM 2017 - Deceiving Network Reconnaissance using SDN-based Virtual Topologies
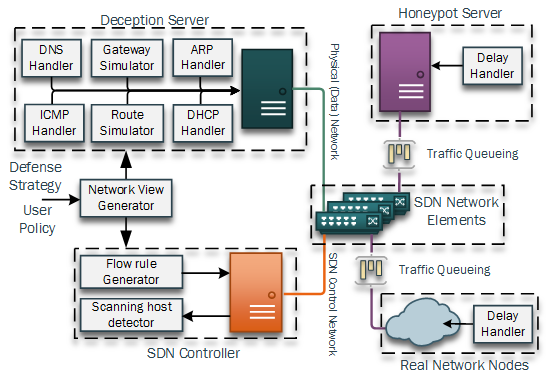
Abstract - Advanced targeted cyber attacks often rely on reconnaissance
missions to gather information about potential targets,
their characteristics and location to identify vulnerabilities in a
networked environment. Advanced network scanning techniques
are often used for this purpose and are automatically executed
by malware infected hosts. In this paper we formally define
network deception to defend reconnaissance and develop a
Reconnaissance Deception System (RDS), which is based on
Software Defined Networking (SDN), to achieve deception by
simulating virtual topologies. Our system thwarts network reconnaissance
by delaying the scanning techniques of adversaries
and invalidating their collected information, while limiting the
performance impact on benign network traffic. By simulating
the topological as well as physical characteristics of networks, we
introduce a system which deceives malicious network discovery
and reconnaissance techniques with virtual information, while
limiting the information an attacker is able to harvest from the
true underlying system. This approach shows a novel defense
technique against adversarial reconnaissance missions which are
required for targeted cyber attacks such as Advanced Persistent
Threats (APT) in highly connected environments. The defense
steps of our system aim to invalidate an attackers information,
delay the process of finding vulnerable hosts and identify the
source of adversarial reconnaissance within a network.
ACM SOSR 2017 - Adversarial Network Forensics in Software Defined Networking
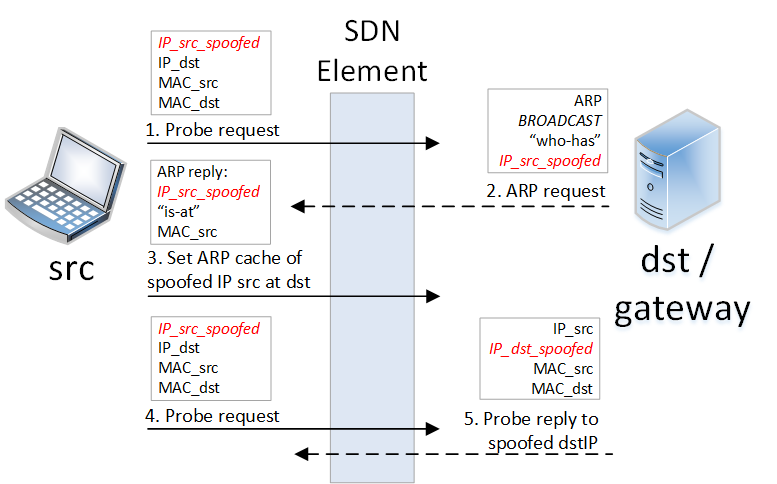
Abstract—Software Defined Networking (SDN), and its popular implementation OpenFlow, represent the foundation for the design and implementation of modern networks. The essential part of an SDN-based network are flow rules that enable network elements to steer and control the traffic and deploy policy enforcement points with a fine granularity at any entry-point in a network. Such applications, implemented with the usage of OpenFlow rules, are already integral components of widely used SDN controllers such as Floodlight or OpenDayLight.
The implementation details of network policies are reflected in the composition of flow rules and leakage of such information provides adversaries with a significant attack advantage such as bypassing Access Control Lists (ACL), reconstructing the resource distribution of Load Balancers or revealing of Moving Target Defense techniques. In this paper we introduce a new attack vector on SDN by showing how the detailed composition of flow rules can be reconstructed by network users without any prior knowledge of the SDN controller or its architecture. To our best knowledge, in SDN, such reconnaissance techniques have not been considered so far. We introduce SDNMap, an open-source scanner that is able to accurately reconstruct the detailed composition of flow rules by performing active probing and listening to the network traffic. We demonstrate in a number of real-world SDN applications that this ability provides adversaries with a significant attack advantage and discuss ways to prevent the introduced reconnaissance techniques. Our SDNMap scanner is able to reconstruct flow rules between network endpoints with an accuracy of over 96%. (Best Student Paper Award)
IEEE INFOCOM 2017 - Stealth Migration: Hiding Virtual Machines on the Network
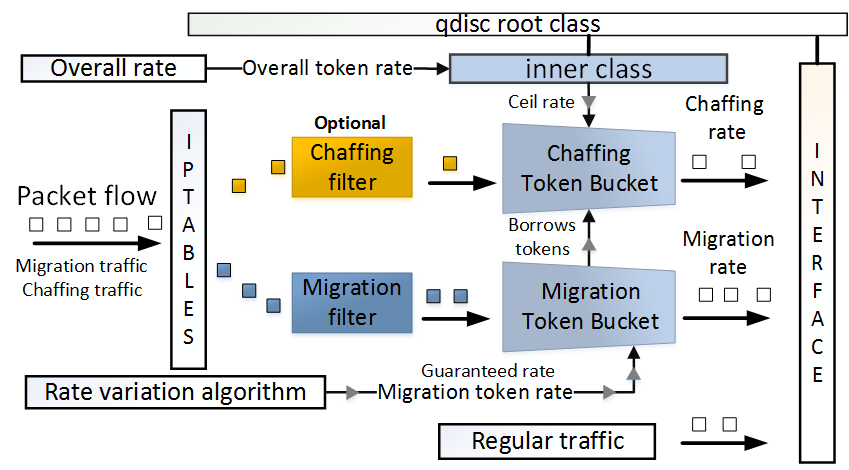
Abstract - Live virtual machine (VM) migration is commonly
used for enabling dynamic resource or fault management, or
for load balancing in datacenters or cloud platforms. A service
hosted by a VM may also be migrated to prevent its visibility to
an external adversary who may seek to disrupt its operation
by launching a DDoS attack against it. We first show that
current systems cannot adequately hide a VM migration from an
external adversary. The key reason for this is that a migration
typically manifests a traffic pattern with distinguishable statistical
properties. We introduce two new attacks that can allow an ad-
versary to effectively track a migration in progress, by leveraging
observations of these properties. As our primary contribution, we
design and implement a stealth migration framework that causes
migration traffic to be indistinguishable from regular Internet
traffic, with a negligible latency overhead of approximately 0.37
seconds, on average.
ACM CCS 2016 International Workshop on Managing Insider Security Threats - Cyber Deception: Virtual Networks to Defend Insider Reconnaissance
Abstract - Live virtual machine (VM) migration is commonly
used for enabling dynamic resource or fault management, or
for load balancing in datacenters or cloud platforms. A service
hosted by a VM may also be migrated to prevent its visibility to
an external adversary who may seek to disrupt its operation
by launching a DDoS attack against it. We first show that
current systems cannot adequately hide a VM migration from an
external adversary. The key reason for this is that a migration
typically manifests a traffic pattern with distinguishable statistical
properties. We introduce two new attacks that can allow an ad-
versary to effectively track a migration in progress, by leveraging
observations of these properties. As our primary contribution, we
design and implement a stealth migration framework that causes
migration traffic to be indistinguishable from regular Internet
traffic, with a negligible latency overhead of approximately 0.37
seconds, on average.
IEEE ICC 2016 - Network Coding Efficiency In The Presence Of An Intermittent Backhaul Network
Abstract - In infrastructure-lacking environments, like mili-
tary areas of operation, the intermittent availability of backhaul
networks leads to greater reliance on peer to peer data exchange.
In such settings, mobile nodes use Delay Tolerant Network (DTN)
protocols for exchanging location specific data. High transmission
delay, packet loss and intermittent connectivity increases the need
for efficient data transmission in such scenarios. In this paper,
we evaluate network coding for efficient data exchange between
mobile wireless nodes under the presence of an intermittent
backhaul network, like a satellite or cellular link. We analyze
the upper bound of savings achievable with network coding for
single-hop packet transmission, and introduce a network coding
algorithm focused on reducing the required number of packet
transmissions in such a setting. Evaluation of our proposed data
exchange protocol shows how network coding can be applied
to reduce transmission delay and minimize the dependency on
an intermittent backhaul network in a communication scenario
typical of a military environment.
IEEE/ACM IPSN 2014 - SIPS: Solar Irradiance Prediction System
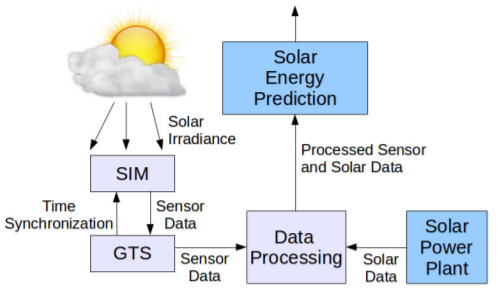
Abstract - There is high interest in up-scaling capacities of
renewable energy sources such as wind and solar. However,
variability and uncertainty in power output is a major concern
and forecasting is, therefore, a top priority. Advancements in
forecasting can potentially limit the impact of fluctuations in solar
power generation, specifically in cloudy days when the variability
and dynamics are the largest. We propose SIPS, Solar Irradiance
Prediction System, a novel sensing infrastructure using wireless
sensor networks (WSNs) to enable sensing of solar irradiance for
solar power generation forecasting. In this paper, we report the
findings of a deployment of a hierarchical WSN system consisting
of 19 TelosB nodes equipped with solar irradiance sensors, and
5 MicaZ nodes equipped with GPS boards, deployed in the
vicinity of a 1 MW solar array. We evaluate different irradiance
sensor types and the performance of different novel prediction
methods using SIPS’ data and show that the spatial-temporal
cross-correlations between sensor node readings and solar array
output power exists and can be exploited to improve prediction
accuracy. Using this data for short-term solar forecasting for
cloudy days with very high dynamics in solar output power
generation –the worst case scenario for prediction–, we get an
average of 97.24% accuracy in our prediction for short time
horizon forecasting and 240% reduction of predicted normalized
root mean square error (NRMSE) compared to state-of-the-art
methods that do not use SIPS data.
IEEE/ACM IPSN 2013 - POEM: Power-efficient Occupancy-based Energy Management System
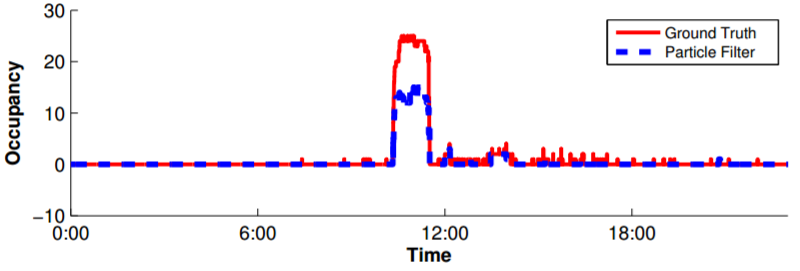
Abstract - Buildings account for 40% of US primary energy consumption and 72% of electricity. Of this total, 50% of the energy
consumed in buildings is used for Heating Ventilation and
Air-Conditioning (HVAC) systems. Current HVAC systems
only condition based on static schedules; rooms are condi-
tioned regardless of occupancy. By conditioning rooms only
when necessary, greater efficiency can be achieved. This
paper describes POEM, a complete closed-loop system for
optimally controlling HVAC systems in buildings based on
actual occupancy levels. POEM is comprised of multiple
parts. A wireless network of cameras called OPTNet is de-
veloped that functions as an optical turnstile to measure
area/zone occupancies. Another wireless sensor network of
passive infrared (PIR) sensors called BONet functions along-
side OPTNet. This sensed occupancy data from both sys-
tems are then fused with an occupancy prediction model us-
ing a particle filter in order to determine the most accurate
current occupancy in each zone in the building. Finally, the
information from occupancy prediction models and current
occupancy is combined in order to find the optimal condi-
tioning strategy required to reach target temperatures and
minimize ventilation requirements. Based on live tests of the
system, we estimate ≈ 30.0% energy saving can be achieved
while still maintaining thermal comfort.