“Cybersecurity impacts all of us”

Welcome! I am Stefan Achleitner, currently leading threat intelligence at Dynatrace.
I am very passionate about the field of cyber-security, specifically cloud and network security as well as the application of Aritificial Intelligence and Machine Learning to detect new threats and attacks.
What's new:
I had the pleasure to talk on the Pure Perform podcast: Why Cyber Defense is Hard: A Closer Look at the latest security research
I had the pleasure to talk on the Pure Perform podcast: Don’t look away from the next cyber security threat with Stefan Achleitner

Published a new blog post about the Spring4Shell vulnerability.
Read more...
I am excited to start a new job at Dynatrace where I am leading the research for Cloud Native Security.

Published a new article on software vulnerabilities on the german technology website Intelligente-Welt.de (Article in German)
Read more...Rewatch my talk on Knowledge Transfer in a Data Driven World at the Austrian Research and Innovation Talks in Washington, DC in September 2021.

Published a new article on password managers on the german technology website Intelligente-Welt.de (Article in German)
Read more...
Published a new article on ransomware on the german technology website Intelligente-Welt.de (Article in German)
Read more...
Published an article on Palo Alto Networks Unit 42 cybersecurity blog on detecting C2 traffic with AI.
Read more...
Published a new article on digital identity on the german technology website Intelligente-Welt.de (Article in German)
Read more...
Published a new article about the new privacy policy on WhatsApp on the german technology website Intelligente-Welt.de (Article in German)
Read more...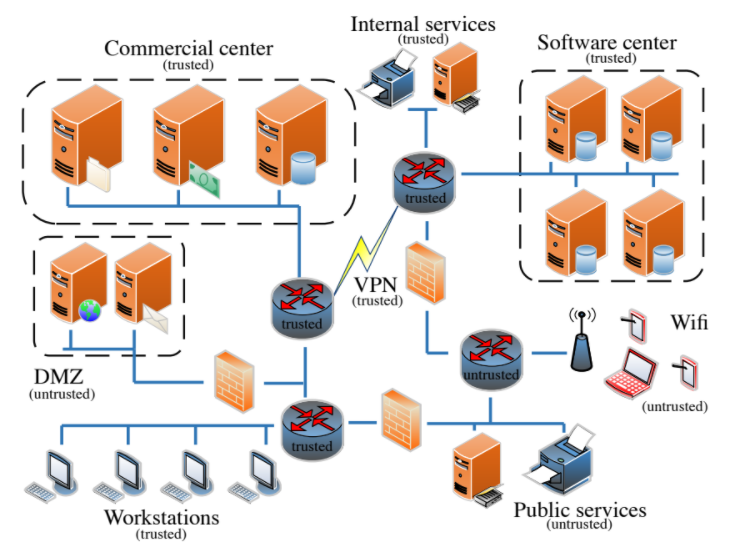
Paper accepted at IEEE Transactions on Network and Service Management
Ensuring that information flowing through a network is secure from manipulation and eavesdropping by unauthorized parties is an important task for network administrators. Many cyber attacks rely on a lack of network-level information flow controls to successfully compromise a victim network. Once an adversary exploits an initial entry point, they can eavesdrop and move laterally within the network (e.g., scan and penetrate internal nodes) to further their malicious goals. In this paper, we propose a novel multilevel security (MLS) framework to enforce a secure inter-node information flow policy within the network and therein vastly reduce the attack surface available to an adversary who has penetrated it. Read more...

Published a new article on the SolarStorm attack on the german technology website Intelligente-Welt.de (Article in German)
Read more...
Research published in a Unit 42 blog on data leakage from Android apps has been featured in Forbes, ZDNet, DarkReading, siliconAngle, Tech Republic, Security Boulevard, Techradar, The Hacker News among others.
Published an article on Palo Alto Networks Unit 42 cybersecurity blog on Android Apps Leaking Sensitive Data.
Read more...
Published a new article on cybersecurity in the home office on the german technology website Intelligente-Welt.de (Article in German)
Read more...
Published a new article on the Corona-App in Germany on the german technology website Intelligente-Welt.de (Article in German)
Read more...
Published a new article on Generative Adversarial Networks on the german technology website Intelligente-Welt.de (Article in German)
Read more...
Interview with the Austrian newspaper "Oberösterreichische Nachrichten" (December 2019, in German)
Read more...

I was honored to give the keynote speech on cyber-security at the Global Fiber Congress 2019
Read more at Dornbirn GFC
Published a new article on social engineering on the german technology website Intelligente-Welt.de (Article in German)
Read more...
Published an article on Palo Alto Networks Unit 42 cybersecurity blog on evasive VPN clients.
Read more...
Published a new article on the security of car to car communication on the german technology website Intelligente-Welt.de (Article in German)
Read more...
Published a new article on differential privacy on the german technology website Intelligente-Welt.de (Article in German)
Read more...
Published a new article on the security of 5G on the german technology website Intelligente-Welt.de (Article in German)
Read more...
Published a new article on cryptomining on the german technology website Intelligente-Welt.de (Article in German)
Read more...
Published a new article on privacy of machine learning on the german technology website Intelligente-Welt.de (Article in German)
Read more...
Paper accepted at IEEE Transactions on Network and Service Management
Software Defined Networking (SDN) provides a framework to dynamically adjust and re-program the data plane with the use of flow rules. The realization of highly adaptive SDNs with the ability to respond to changing demands or recover after network failures or attacks in a short period of time, hinges on efficient updates of flow rules. Read more...

Published a new article on next generation of Spectre and Meltdown on the german technology website Intelligente-Welt.de (Article in German)
Read more...
I received The Graduate Scholarship for Excellence in Engineering Thank you Penn State!
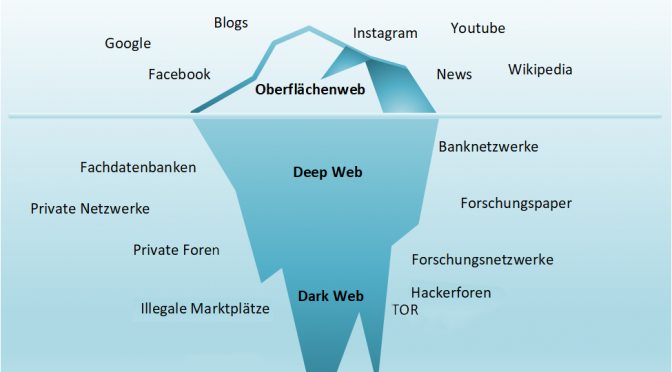
Published a new article on the Deep- and Dark-web on the german technology website Intelligente-Welt.de (Article in German)
Read more...
Published a new article on the security of the Internet of Things on the german technology website Intelligente-Welt.de (Article in German)
Read more...
Published a new article on spectre and meltdown on the german technology website Intelligente-Welt.de (Article in German)
Read more...
Published a new article on the security of machine learning on the german technology website Intelligente-Welt.de (Article in German)
Read more...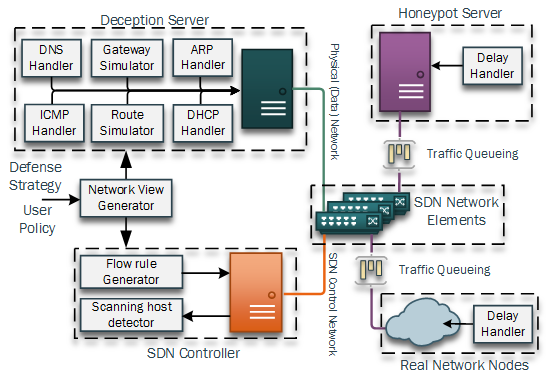
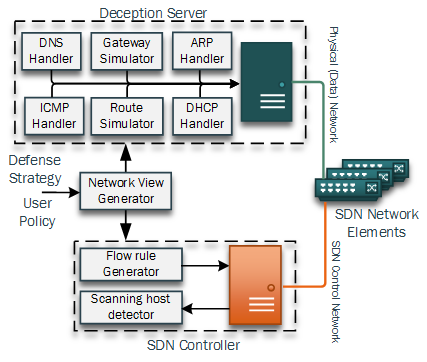
Paper accepted at IEEE Transactions on Network and Service Management, Special issue on Advances in Management of Softwarized Networks
Advanced targeted cyber attacks often rely on reconnaissance missions to gather information about potential targets, their characteristics and location to identify vulnerabilities in a networked environment. Advanced network scanning techniques are often used for this purpose and are automatically executed by malware infected hosts. Read more...

Published a new article on ransomware on the german technology website Intelligente-Welt.de (Article in German)
Read more...
Our work on Adversarial Network Forensics in SDN won the Best Student Paper Award at the 2017 ACM Symposium on SDN Research (SOSR)
Read more...New attack vector on SDN:
SDN has many security issues, adversarial network forensics is a new attack vector on SDN. Check out these videos where I show how SDNMap can bypass an the Access Control List in Floodlight and reconstruct a Load Balancing Policy modeled after OpenStack Quantum: Read more on adversarial forensics in SDN...
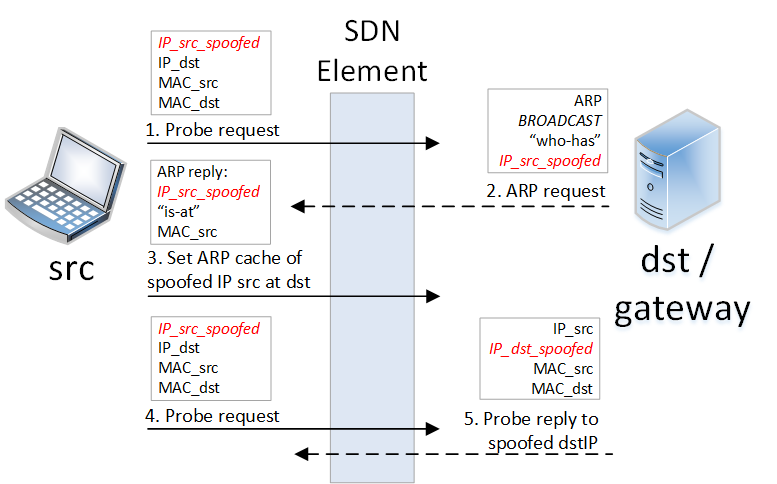
Paper at 2017 ACM Symposium on SDN Research (SOSR)
The essential part of an SDN-based network are flow rules that enable network elements to steer and control the traffic and deploy policy enforcement points with a fine granularity at any entry-point in a network. The implementation details of network policies are reflected in the composition of flow rules and leakage of such information provides adversaries with a significant attack advantage such as bypassing Access Control Lists (ACL), reconstructing the resource distribution of Load Balancers or revealing of Moving Target Defense techniques. In this paper we introduce a new attack vector on SDN by showing how the detailed composition of flow rules can be reconstructed by network users without any prior knowledge of the SDN controller or its architecture. Read more...
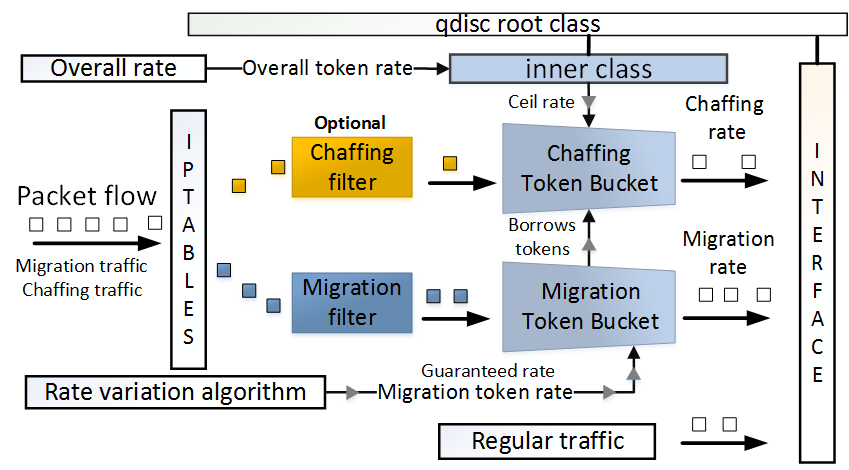
Paper to appear in 2017 IEEE International Conference on Computer Communications (INFOCOM)
Live virtual machine migration is commonly used for enabling dynamic resource or fault management, or for load balancing in datacenters or cloud platforms. A service hosted by a VM may also be migrated to prevent its visibility to an external adversary who may seek to disrupt its operation by launching a DDoS attack against it. We design and implement a stealth migration framework that causes migration traffic to be indistinguishable from regular Internettraffic, with a negligible latency overhead. Read more...

Systems and Technology Engineering internship at Ericsson
From May to August 2016 I worked for Ericsson in San Jose, CA as a systems and technology engineering intern. I developed a security/cryptography service module in C and OpenSSL for Ericsson's IPOS platform. The goal of this project was to make cryptography easy to use by automizing procedures such a key generation, sensitive data storage, crypto algorithm selection, etc. in an intelligent way. Read more...